ClamAV
Plugin-Download (requires login)
With the free ClamAV plugin for Xima® Formcycle it is possible to scan uploaded files for viruses. For this purpose, this plugin establishes a connection to a ClamAV daemon service via TCP.
Functionality
- Immediate virus scan
- Each file is scanned immediately after upload.
The used ClamAV-daemon service can neither be configured nor started by this plugin.
Installation
The installation of the plugin has to be carried out via the interface of plugins provided for this purpose. Only the corresponding jar file has to be installed.
Plugin configuration
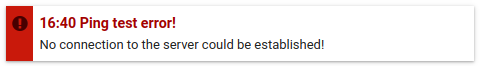
After saving, a ping test is automatically performed. If this fails, a message will be displayed. In this case all uploads in the backend or in the form will be marked as faulty - the plugin should be deactivated first and a working connection should be established.
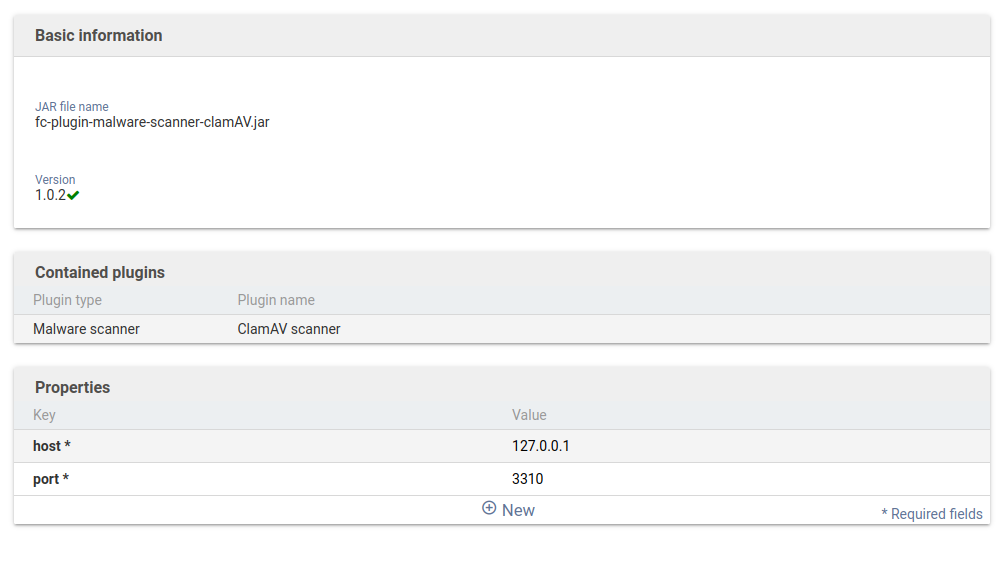
The following configuration parameters exist:
- host (Required)
- Default value: 127.0.0.1. Specifies the IP address of the ClamAV-daemon service to be used. The default value is 127.0.0.1 and thus uses a local ClamAV-daemon service.
- port (Required)
- Default value: 3310. Specifies the port of the ClamAV-daemon service to use. The default value should only be changed if this port is not available.
- os (Optional)
- Default value: JVM_PLATFORM. Operating system on which the ClamAV daemon service is running. This value is only relevant if the operating system of formcycle and that of the ClamAV daemon service are different. For Linux or MacOS enter UNIX, for Windows enter WINDOWS. If both are running on the same operating system, you can leave this value blank or use JVM_PLATFORM.
Configuration ClamAV
The following section discusses installation and configuration of ClamAV. Our recommended scenario is to install Xima® Formcycle and the ClamAV-daemon service on the same server.
Installation
To install ClamAV on a server, the following commands should be entered on the server.
ClamAV is the program that can scan files for viruses and is required for the use of ClamAV-daemon.
- Update the package list:
- sudo apt-get update
- Install ClamAV and ClamAV-daemon:
- sudo apt-get install clamav clamav-daemon -y
Update the virus signature database
freshclam is automatically installed with ClamAV and is used to update the virus signature database.
- Terminate the automatic freshclam process:
- sudo systemctl stop clamav-freshclam
- Manually update virus signature database:
- sudo freshclam
Configuration ClamAV-daemon
ClamAV-daemon is the process running in the background on the server, which is addressed for the virus scan. This is done via TCP and must be configured accordingly.
For this purpose, the configuration file under: /etc/clamav/clamd.conf should be adapted.
Open the configuration file:
- sudo nano /etc/clamav/clamd.conf
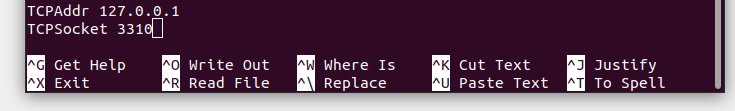
Use the arrow keys to navigate to the end of the file.
- Add TCPAddr 127.0.0.1
- Add TCPSocket 3310
- Specify root rights for ClamAV-daemon
- To do this, the row User clamav has to be changed to User root in this file.
Now you can save and exit with Ctrl + X. Confirm with Y and the Enter key.
Starting the ClamAV-daemon Service
Now the service can be started.
- Start the ClamAV-daemon Service:
- sudo systemctl start clamav-daemon.service
Checking the availability of the service
In order for this plugin to be able to address the ClamAV-daemon service, the service must be listening in the right place - in this case at 127.0.0.1:3310. This can be checked in the server's terminal.
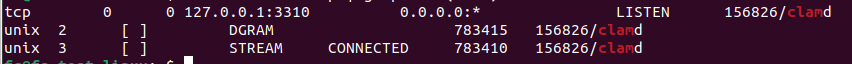
Using netstat the TCP socket of the ClamAV-daemon service can be examined.
- sudo netstat -anp | grep -E "(clam)"
If no line starting with tcp is seen or a different host:port combination is seen as 127.0.0.1:3310, the configuration has to be checked again.
Example configuration
An example configuration with the above default values:
Usage
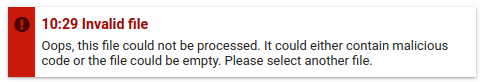
As soon as a virus signature has been detected, the following message is displayed:
Test file
A common method for checking virus scanners is the eicar.com file.
At any point this test file can be uploaded and after successful configuration the message shown above should be seen.
Logging
ClamAV creates logs which can be found under /var/log/clamav/clamav.log .
For example, after uploading the eicar.com test file, the following entry can be seen in clamav.log :
- Wed May 25 10:10:21 2022 -> instream(127.0.0.1@32984): Win.Test.EICAR_HDB-1(44d88612fea8a8f36de82e1278abb02f:68) FOUND
Xima® Formcycle logs can be found for this at /formcycle-data/formcycle7/logs .
After uploading the eicar.com test file, for example, the following entry can be seen in formcycle-errors-log :
- [WARN] [25-05-22 10:10:21,192] [ajp-nio-127.0.0.1-8009-exec-43] (MalwareScanner.java:211) - Scanner <fc.plugin.malware.scanner.clamAV. ClamAntiVirusFileScanner@7b2a4953> detected malware signature for file </home/fc/tomcat9/tmp/xima-temp/formcycle7/xfc-malware-scan/stream-scan12705251110052849842/data2383296604287452271>: {stream=[Win.Test.EICAR_HDB-1]}
- [ERROR] [25-05-22 10:10:21,207] [ajp-nio-127.0.0.1-8009-exec-43] (VirusScannerService.java:71) - Detected a virus
Version history
Version 1.0.3
- Change: The plugin is synchronized with the frontend server when one is available. This allows for malware scanning when using a frontend server.
Version 1.0.2
- Remove: property for path scanning, only InputStream now.
Version 1.0.1
- Fix: Skip scanning if operating system is not UNIX instead of detecting the file as a virus.
Version 1.0.0
- Initial release